The Main Kind of Message Queue
January 19, 2025 · 12 min read · Page View:
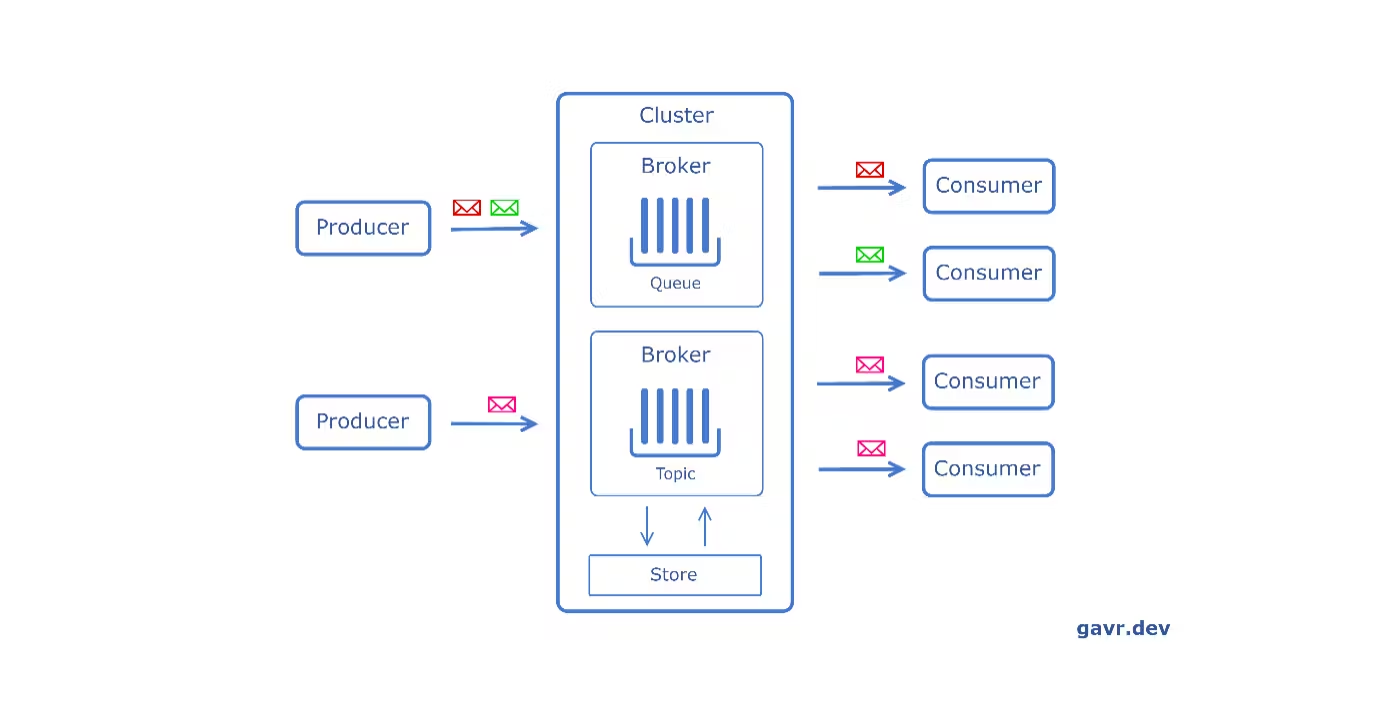
Message queues are a form of asynchronous service-to-service communication. They are important in enhancing a system’s scalability, reliability, and maintainability.
...
Message queues are a form of asynchronous service-to-service communication. They are important in enhancing a system’s scalability, reliability, and maintainability.
...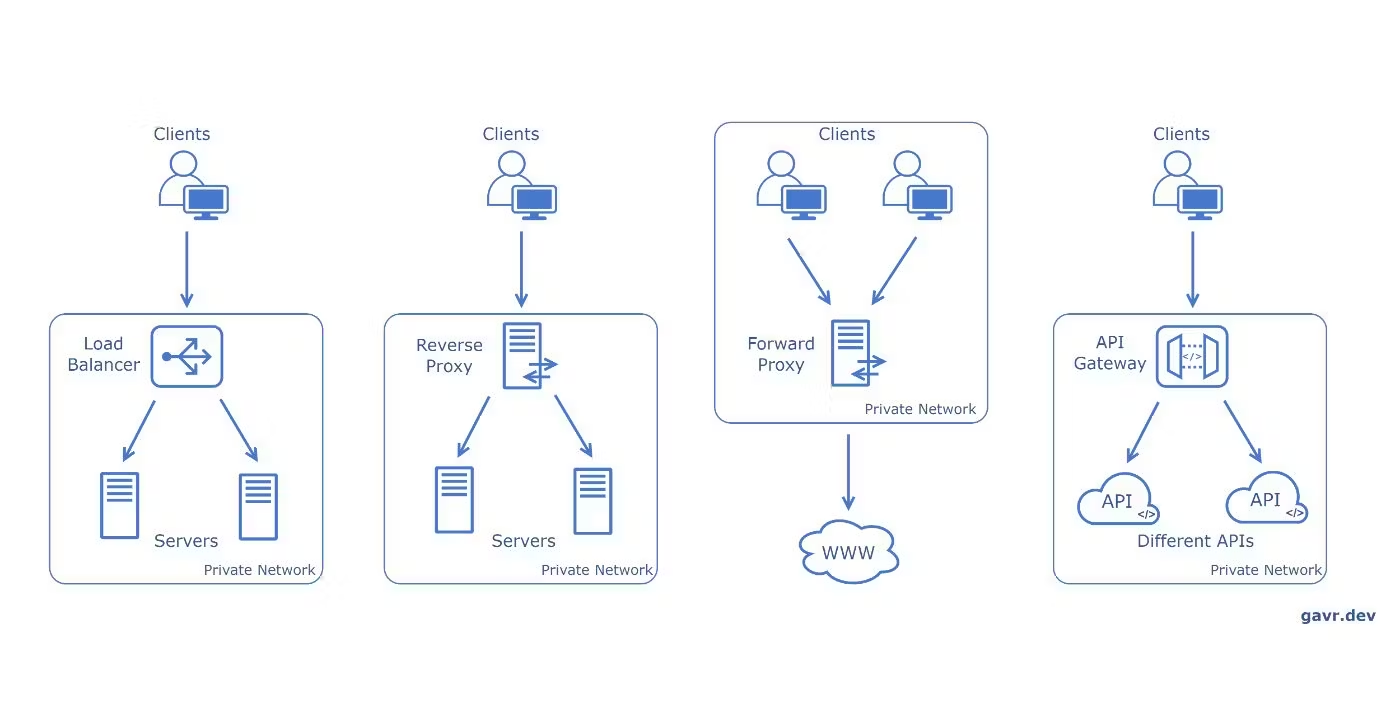
Do you know the basic method to manage the traffic? There are four methods: Load Balancers, Reverse Proxies, Forward Proxies, and API Gateways. And they have different features and usage scenarios.
...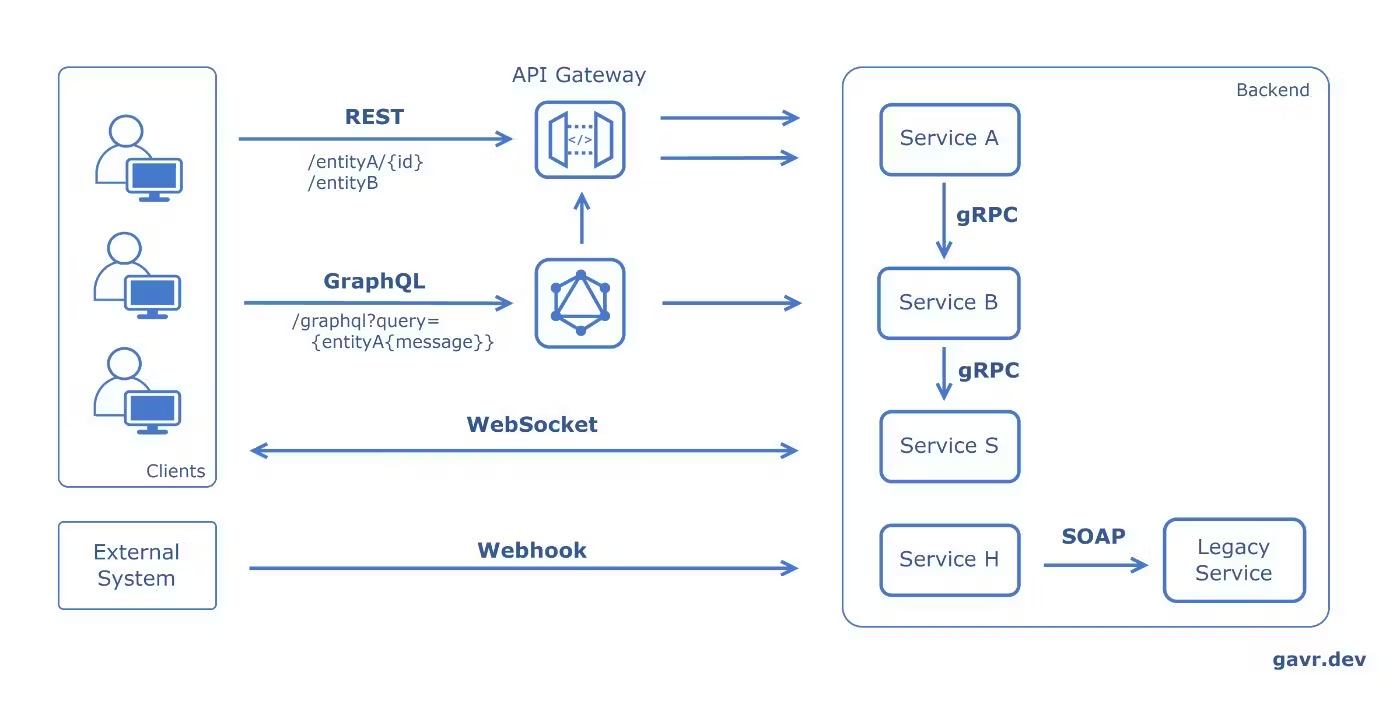
In the daily life, we often hear about different kind of API, such as REST API, GraphQL API, WebSocket, Webhook, RPC and gRPC even the SOAP, so do you know the difference between them? How to choose the right API for your project?
...Do you really know the encode and decode in Python?
...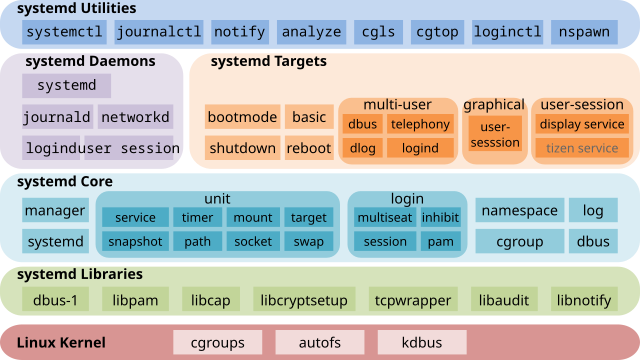
It has been a long time since the linux used init to manage the startup process, such as sudo /etc/init.d/apache2 start or service apache2 start, but the init is serial. To address this issue, the systemd was born. The d is the abbreviation of daemon, which means the systemd is a daemon manager. The systemd substitutes the initd and becomes the default main process PID 1.
Normally, we often write a Dockerfile in the current directory.
Dockerfile is a configuration file that describes how to build the image. You can refer to the official documentation[1] for more details.CMD, only the last one takes effect. So if you have multiple commands to run, you better write them in a script file.systemd in the container. Its startup program is the container application process. The container exists for the main process. Once the main process exits, the container loses its meaning of existence and thus exits. So when you execute multiple commands and if they are blocking, you better write the previous commands in nohup and the last command in the blocking command. (never use the command such as CMD service nginx start, the CMD only will execute as CMD [ "sh", "-c", "service nginx start"], when the sh is executed, the container will exit, the correct way is run it directly CMD ["nginx", "-g", "daemon off;"])
Docker is a practical tool for everyday use, and like Git, you can learn it in just 30 minutes.

So what is the difference between the Instance method, the Class method and the Static method?
...
In today’s digital age, security is paramount. As we increasingly rely on technology for communication, commerce, and data storage, understanding the fundamentals of security becomes essential. This article provides an overview of key security concepts, including encryption, digest algorithms, and digital signatures. By exploring these topics, we aim to equip you with the knowledge to protect your digital assets and ensure the integrity and confidentiality of your information. Whether you’re a tech enthusiast or a professional in the field, this guide will offer valuable insights into the mechanisms that safeguard our digital world.
...
Last week, I have made a python cli tool. To make it more convenient to use, I want to publish it as a pip module, so I have made some research and mistakes, and finally succeeded.
...