Cloudflare Warp
June 6, 2025 · 7 min read · Page View:
The warp+ service in Cloudflare
If you have any questions, feel free to comment below. Click the block can copy the code.
And if you think it's helpful to you, just click on the ads which can support this site. Thanks!
Frankly speaking, the first time I heard about Cloudflare is the service so called Cloudflare WARP which is provided by Cloudflare. Nowadays, you must have heard the fastest and private network can be provided by Cloudflare. If I say Cloudflare achieves the fastest object by the first step to visiting any website, the world’s fastest public DNS 1.1.1.1. You can probably guess the private provider, yes, that is Cloudflare WARP. So this article I will introduce the Cloudflare WARP further zero trust and how to use it.
What is Cloudflare WARP #
Actually you can recognize it as a VPN application, it based on the WireGuard protocol, and it is called as BoringTun.
Why we use Cloudflare WARP #
Through the WARP, your traffic will be encrypted and sent to Cloudflare’s network, and then be sent to the destination server, ensuring that no one in between is snooping on what you’re doing.
Besides, if the destination is also cloudflare customer, the resources will be returned immediately through cdn network.Otherwise, for the WARP+ will use Argo Smart Routing to visit data center fastest.
Basically, the connect between app and website is encrypted, but the process that lookup for the DNS is not.To address this issue, you might use the DNSoverHTTPS or TLS to encrypt the DNS lookup process. If you are not familiar with these, you can refer to my previous article A brief introduction to DNS[1]。
What is the principle of Cloudflare WARP #
In short, cf routers listen on Anycast IP addresses which are advertised over the public Internet. So for the user connects to the resources hosted on Cloudflare, each networking device their packets pass through will choose the shortest path to the nearest Cloudflare data center.
The connection process will use the WireGuard protocol to encrypt the traffic. Because the WireGuard is based on the UDP protocol, it uses a session key negotiated with public-key encryption to secure the contents of that UDP packet.
Basically, you can reckon that the WARP is the TCP message is wrapped by the encrypted UDP packet.
Why use UDP to wrap the TCP message? #
The reason for the solution is based on the trade-off between the performance and the stability.
As we know that, for most communication, we use the TCP protocol. The TCP protocol is reliable, orderly. It introduces the concept of port.
Scenario #
Imagine that, if you send a search request to the google. What it happens? I think most people who learned the network course will know that, is you send a TCP packet from your device port(say that ip:12.34.56.78, port:52111) to the google server(eg. ip:198.41.215.162, port:443 https).
However, that is the very ideal scenario. The ipv4 address is already allocated up. So there won’t be many address for every one. Then the ISP introduces the NAT(Network Address Translation) to solve the problem.
Here, I really recommend the image which is from the Cloudflare’s blog[2].
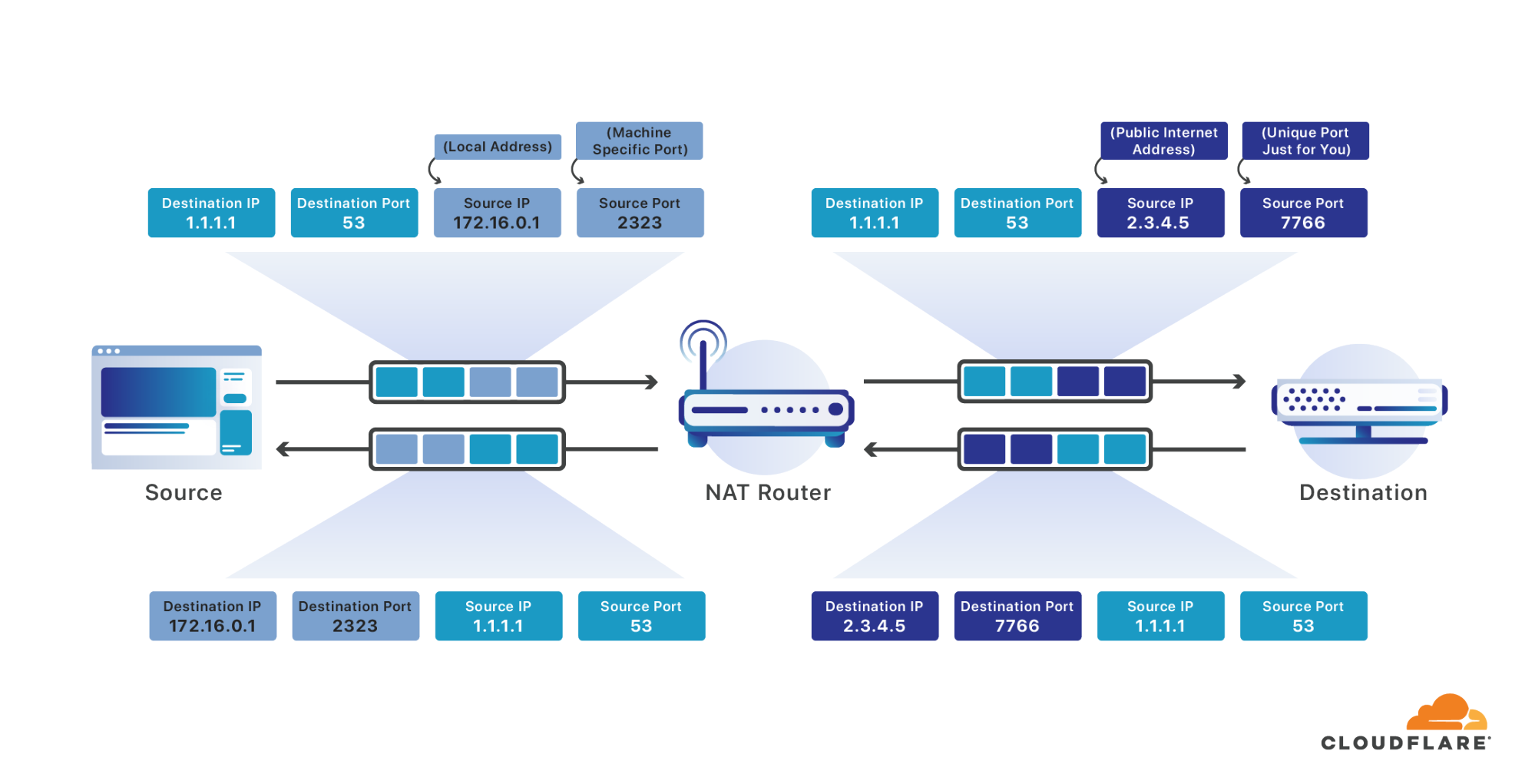 NAT
NATAs you can see, the NAT router will allocate a local address and port for your device, then forward your request to the destination using the router public ip and port, also the router will reserve the mapping between your device local ip port with destination ip and port. Every time your send request, the router will replace the request’s source ip and port, and when you receive the response, the router will replace the response’s destination ip and port with your local ip and port.
However, that’s the problem, for the WARP session, the process will last at least 30 seconds. But when the session is outdated, the router will delete the mapping, and wait for the next request. You may be curious about why the cloudflare not use the TCP Long Connection?
Don’t forget, exactly the long connection can resolve the problem somehow, but most of the usage is on the mobile device, if there is always a Keep-Alive message which is sent by your mobile device, your battery will be consumed more. I think it’s the same situation that you will never expect your phone always in the streaming or a live show. Besides, your connection will be always changed, if you change your data from wifi to cellular, the connection has to be re-established.
UDP #
We know that UDP is the protocol designed for the real-time communication. It’s not reliable, not orderly. But it’s fast. So the solution that using UDP to wrap the TCP message is the best choice. UDP for the connection, and TCP for the message reliable.(If the UDP packet is lost, then resend. This will be more efficient than TCP on TCP encryption.)
The WireGuard is based on the UDP protocol. It uses a session key negotiated with public-key encryption to secure the contents of that UDP packet. To make cloudflare load balancing technique work though there is needed a way to identify which client a WARP packet was associated with before it could be decrypted.
So before you can decrypt the contents, what you can check are the ip header, the UDP header, and the WireGuard header. Actually we cannot get the four pieces of information(src ip port, dst ip port). So we have to find a way to identify the client. The WireGuard header is as follows:
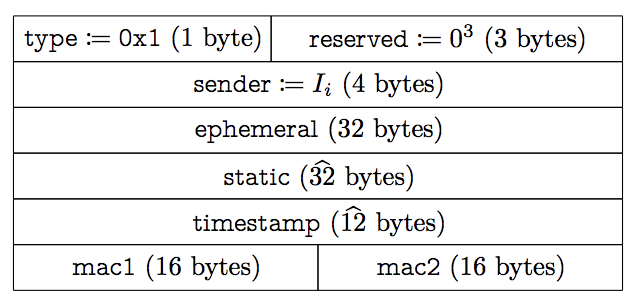
The cloudflare use the reserved bytes to be the client id, which is generated by the cloudflare auth server. Also its only 3 bytes, around 24 bits, which is not enough for all the client, but that’s not a track usage, just as the mapping in the router, so these bytes are enough for loading the balance.
For the technical details, I strongly recommend the The Technical Challenges of Building Cloudflare WARP[3].
WARP+ #
So what is the difference between WARP and WARP+? I find a example[4] can explain it.
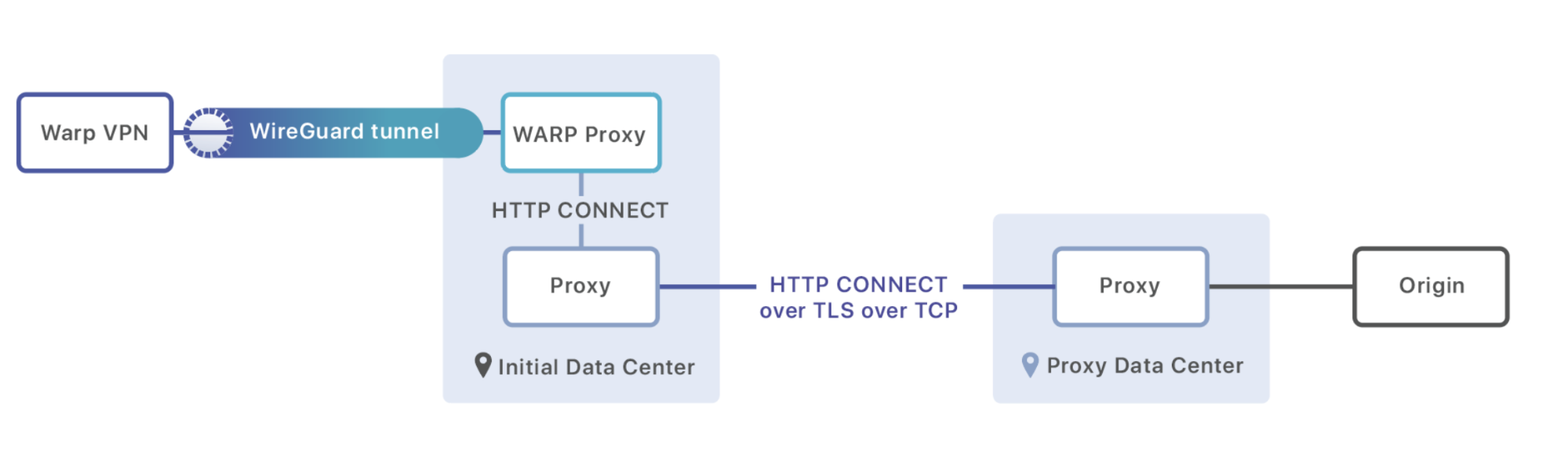
Normally, when the user send a request, and visit the origin server, and if the request not hit the cdn, so the cdn data center needs to forward the request the origin server.
In the example, the user sends a request from hk to the server in sgp. And the request not hit the cdn cache, so the data center(which is hit by user) sends the request to the origin server. In short, in warp, the request to the origin server is sent by the data center which first hit by the user.
And the same request, if in the WARP+, as the user tries, the request is sent by the data center which is nearest to the origin server(in other words, the distance between the nearest data center and the hit data center(initial data center) is using the cloudflare own line which is called as Argo[5], the best router).
 The WARP+
The WARP+Teams #
In cloudflare, you can create a team, through which you will have 50 seats to use the WARP+ service for free (precisely speaking, that is WARP for team).
When you use the Cloudflare zero trust warp for teams, your ip will be the initial data center(first hit) of the Cloudflare. Here, when I connect to the warp in shenzhen, the ip address request to the target website displayed is the shanghai data center ip of Cloudflare.
In mainland, you probably sometimes have certain chance to connect warp server. If you encounter some error, you can refer to the troubleshooting[6] for more details.
About the privacy #
Now, you must have learned a lot from the example above. You may be curious about that since your request is forwarded by the proxy server in cloudflare data center, so will the proxy server expose your real ip address?
As the cloudflare blog WARP is here (sorry it took so long)[7] says: From a technical perspective, WARP is a VPN. But it is designed for a very different audience than a traditional VPN. WARP is not designed to allow you to access geo-restricted content when you’re traveling. It will not hide your IP address from the websites you visit.
But as we have analyzed above, only the communication between you and the cloudflare is encrypted by the WireGuard protocol. Actually your request will be sent to the origin server, if the origin server:
- is a cloudflare customer: your ip might be provided by the cloudflare.
- is not a cloudflare customer: the tcp connection will be the cloudflare proxy server and the origin server, so the origin server will not know your real ip address.
You can try this website: https://www.cloudflare.com/cdn-cgi/trace[8] to check if your ip is using warp.
Then you can request the website to check if the website is hosted on cloudflare. Some website on the cloudflare will display your real ip address. But for those don’t, it will only display the cloudflare ip address.
References
- https://blog.timerring.com/posts/a-brief-introduction-to-dns/ ↩︎
- https://blog.cloudflare.com/warp-technical-challenges/ ↩︎
- https://blog.cloudflare.com/warp-technical-challenges/ ↩︎
- https://blog.skk.moe/post/something-about-cf-warp/ ↩︎
- https://www.cloudflare.com/application-services/products/argo-smart-routing/ ↩︎
- https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/troubleshooting/client-errors/#CF_HAPPY_EYEBALLS_MITM_FAILURE ↩︎
- https://blog.cloudflare.com/announcing-warp-plus/ ↩︎
- https://www.cloudflare.com/cdn-cgi/trace ↩︎
Related readings
- The principle of Cloudflare SaaS Optimization
- The MitM and HTTPS Capturing
- The Practice of Resolving Domain
- The Iftop
- The Method to Manage Traffic
If you want to follow my updates, or have a coffee chat with me, feel free to connect with me: