Real Computer Network
December 23, 2024 · 16 min read · Page View:
Generated by DALL 3
If you have any questions, feel free to comment below. And if you think it's helpful to you, just click on the ads which can support this site. Thanks!
For the computer network, I believe that most people have learned it in the course of university or college. No matter whether you are familiar with it or not, this article will give you a different perspective of the network. It can really help you a lot.
Basic concepts #
Providers #
IDC: Internet Data Center, which is the data center of the internet. It is the place where the servers are located.
ISP: Internet Service Provider, which is the internet service provider. It is the company that provides the internet service.
Main Public Cloud Service Providers:
AWS: Amazon Web Services, which is the cloud service of Amazon.Azure: Microsoft Cloud Service, which is the cloud service of Microsoft.Alibaba Cloud: Alibaba Cloud, which is the cloud service of Alibaba.GCP: Google Cloud Platform, which is the cloud service of Google.PCCW(Recommended): Pacific Century CyberWorks, which is the internet service provider of Hong Kong, China.(make sure it is Two-way instead of one-way)
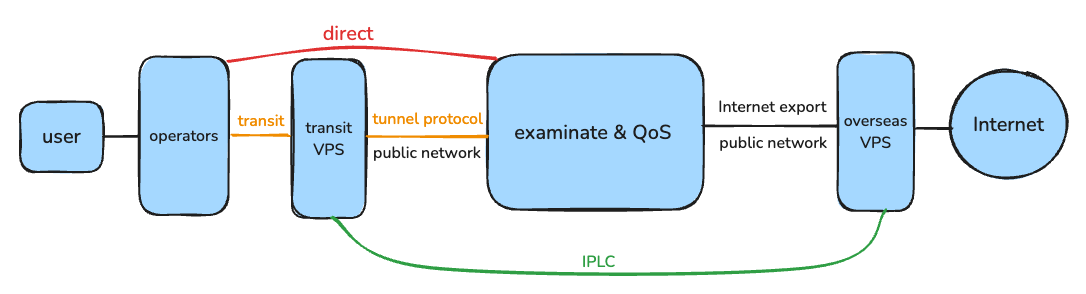
Besides, if your neighbors(the shared users of the server) are all “one-click script” masters, using serverspeeder, violent modification BBR, KCPTun multiple times more packet sending, etc. But you don’t do any optimization, then even you have a whole submarine cable, you will still be slower than them.
When you buy a VPS, the bandwidth is provided by the operators which the VPS supplier purchase from the operators.
Network Circuits #
Public Network #
You can check your network AS info here: https://ipinfo.io/
International export: The international export is the last port of the internet in China when the traffic is going to the overseas. Mainly located in Beijing, Shanghai and Guangzhou.163:AS4134. The 163 network is the backbone of the internet in China. And mainly used by China Telecom. The backbone node is started with202.97.
There is basically no performance bottleneck when accessing each other within the 163 network in China. Congestion only occurs at the international export..
169:AS4837. The 169 network is the backbone of the internet in China. And mainly used by China Unicom.AS 9929: Also known as the former China Netcom Internet (CNCNET). The AS number of China Unicom’s A network backbone is 9929. It was built by the China Netcom, and after the merger of China Netcom and China Unicom, so the A network was available. Now the users are less and mainly aims for the government.AS9808: TheAS9808is the backbone of the internet in China. And mainly used by China Mobile. ThePCCW lineis currently among the lines between China and Hong Kong, China or those from China to other regions in Southeast Asia where transshipment in Hong Kong, China is required. It is the line with the best quality in China except for the pureCN2 GIAline.Educational Network/China Science and Technology Network/Private Broadband.CN2(CNCN): China telecom next carrier network, which is the backbone of the internet in China(Public network), which is more advanced than the old 163 network. The backbone node is started with59.43.CN2GT: CN2 Global Transit, cheaper but congested, in CN2 GT product in the city → province → international export section is 163 network, the international export → overseas access point section is CN2 network, the return is the same.CN2GIA: CN2 Global Internet Access, expensive but less congested.(eg. Bandwagonhost has the most stable and cheapest CN2GIA line, but it is the key examined object of domestic.) GIA the whole network is CN2 network.
Dedicated Network #
IPLC: International Private Leased Circuit, which is the international dedicated line.
But for many service suppliers, it is just the intranet of Alibaba(
深港means Alicloud shenzhen – Alicloud HK), which usually purchase multiple end to end IPLC lines to connect the every data center. Then it has two pros:
- The bandwidth in
IPLCis dedicated, which is more stable than public network.(The decicated line is normally described the physical line, the most traffic inSubmarine optical cableis the public network traffic and small part is theIPLCtraffic.)- The traffic when transiting, it will not go through the specific examination.
IEPL: International Ethernet Private Line, which is the enhanced version of IPLC. It is a dedicated management bandwidth service from end to end.
Anycast: it is a network technology that allows a single IP address to be broadcast to multiple locations. That means the IP will be the same, but the location is different.
This IP address is in the physical link between domestic and abroad. When users access this IP address, they will be connected to the nearest server. Just like the CDN. The cons:
- The bandwidth is bind to the single IP address, so if it was DDOS, it is hard to deal with it.
- Expensive.
Service Concepts #
The three major operators are paid inter-network settlement, which means the traffic you consume is across the operators, they will pay the cost internally.
QoS: Quality of Service, which is the service quality of the network. It can dynamically adjust the priority of the traffic, such as video calls(bandwidth first), online games(latency priority), etc.
SLA: Service Level Agreement, which is the agreement between the supplier and the user. It is the service level of the supplier.
BGP: Border Gateway Protocol, which can dynamically select the best route.(when you buy vps, you can easily find it on the supplier website) Which means the same IP in multiple operator’s network is directly connected.
Redirect: Redirect data from one server to another. Alibaba Cloud public network transit is more common in small-scale suppliers redirect.
Port: The port is the communication endpoint of the network. It is the port of the server.
IP #
IP database #
IP Database stores IP address and physical address mapping.
- The most used domestic IP database is IPIP.
- The overseas is MaxMind.
Cellular Base Station #
When using the cellular network, the IP address is the private IP address, and then it will be converted to the public IP address through the NAT. This situation leads to everyone using the same IP segment to access websites or apps. Generally, we refer to these relatively fixed IP segments as base station IP addresses.
- So it is hard to locate the IP address to the specific city, which means the same IP address can be in different cities. And sometimes a series of IP is assigned to the 2~3 cities.
- Due to the
NAT,every IP address corresponds to many users, so suspending the IP address will affect many users. Roaming: When you are roaming, the IP address will be changed. It’s mainly has three operators:- mobile: roaming to the local network. If your card is in Beijing, and you go to Shanghai, then you will see the IP of Shanghai.
- Unicom and Telecom: roaming back to the local network. If your card is in Beijing, and you go to Shanghai, you will still see the IP of Beijing.
- So that accounts for the reason why you are using your card abroad, you are still blocked to visit websites. Cause you are roaming back to china and then try to access the websites.
Check IP #
IP question #
Why the ip is not correct?
- You are using the phone to test? (It is the base station’s fault)
- What is your current operator? (If it is the secondary operator, it is the fault of the third-party export)
- What browser are you using? (It is the cloud acceleration’s fault)
What is the third-party export?
Every operator will not only have their customers, but also have to obtain the network export, but the backbone networks are built by primary operators. So if the secondary operator wants to access the internet, it will have to pay the access fee to the primary operator. The primary operator avoids the competition, so it will bring up an expensive fee. But some people in the primary operator will sell them in a lower price, which is usually used by the secondary operator informally.
IP attribution #
The IP attribution identified based on your access purpose: Residential broadband, Business broadband, IDC, etc.
Native IP #
Native IP: The operator’s IP address. Broadcasting country is generally the same as registration country. Normally, it can used to unlock the hulu, netflix, etc. Because the Native IP is generally not used to the cloud computing service or have a good reputation.
Broadcast IP: The IP address of the VPS is not the same as the location of the VPS. That means this IP is from another country / region.
Streaming media unlock: Many streaming media platforms will restrict the specific IP access due to the copyright issues. Generally, the network operators(eg.HKT) have their own IP, which is used in commercial or Residential broadband. And the IP won’t be blocked because they are all the objective customers. Besides, the Residential broadband is hard to blocked because it is dynamic.
Protocols #
Shadowsocks: the fastest rtt.
ShadowsocksR.
V2Ray(Vmess is the self protocol, V2Ray is the collection of protocols): more handshakes, which means slower rtt. Vmess + TLS encryption + websocket, which is more stable.
Trojan: fix some cons of V2Ray. The core is only websocket + TLS. (TLS is the most secure which banks are using). It imitates the normal http request and works on the 443 port. If it receives the illegal request, it will provide service, or it will transit the traffic to nginx, and the nginx deal with the request. Its behavior is similar to nginx, so it is hard to detect. Meanwhile, in order to avoid the malicious detection, it will redirect the 80 port traffic to the 443, and only open the 80 and 443 port, which is similar to the normal web server.
obfs (simple-obfs): it is a tool that can encrypt the traffic. It can be used to avoid the detection. obfs has two modes, one is HTTP, the other is TLS.
DNS #
DNS is the domain name system, which is the system that can translate the domain name to the IP address.
No matter how we use PPPoE to dial up or connect the optical cat through DHCP, the Internet service provider (ISP) will send you two DNS. For convenience, I call these two DNS as ISP DNS.
In the DNS resolution process, the user initiates a request to the recursive DNS, and the recursive DNS requests the resolution result from the authoritative DNS. In other words, the recursive DNS plays a forwarding role. The ISP’s DNS is a recursive DNS; at the same time, some individuals or Internet service providers also set up their own recursive DNS for everyone to use, which is called public DNS.
Some famous public DNS:
- Cloudflare DNS:
1.1.1.1,1.0.0.1 - Google Public DNS:
8.8.8.8,8.8.4.4 - Alidns:
223.5.5.5,223.6.6.6 - Tencent DNSPod:
119.29.29.29,119.28.28.28
For most people, the ISP DNS provided by the operator should be the most accurate and suitable, with a short response time and the most accurate CDN resolution result.
But the operator often does DNS pollution, it will lead the user to their cache server or some advertising mirror website or tamper the TTL, which will lead to the DNS load less.
But the public DNS does not accelerate the resolution speed. Public DNS is a local DNS service provided by some enterprises, which usually provides one or more Anycast IP addresses, but actually has multiple cluster services.
When users go online, the client will request the resolution from the A address in the cluster, this A address is called DNS entry; the public DNS will use the B address in the DNS cluster to compare with the IP library when judging the user’s source, this B address is called DNS exit.
So in the process of going online, users will get the resolution from the DNS entry, and the NS server will allocate the intelligent resolution to the DNS exit. If the DNS entry does not have the requested resolution cache, it will request the upper DNS to query, and finally request to the NS server, till then the user get the resolution result.
Hence, when the DNS entry and the DNS exit are inconsistent with the user’s actual network, it may lead to the DNS resolution result not being the optimal.
CDN #
CDN is the content delivery network, which can provide the content to the user faster and more reliable via the nearest server.
Besides, the DNS exit is very important for CDN. The public DNS is essentially forwarding your query request to the upstream DNS; without EDNS, the authoritative DNS of the CDN will determine your operator and your location based on the request IP used by the public DNS (that is, the DNS exit), and then return the nearest node IP. In brief, CDN will return the nearest IP to the DNS exit.
For more information, you can refer my article A brief introduction to DNS
Proxy #
Every traffic transit in public network across the countries will be examined.
The proxy means that the traffic is go through the proxy server.
Proxy Types #
The basic proxy methods are mainly three types:
- Software Proxy:
- VPN: virtual private network which can ensure the end-to-end communication security. But nowadays, it might remains some risks.
- Encrypted traffic: mainly exists in the Shadowsocks, SSR, V2Ray and Trojan protocols, which usually encrypt the traffic locally and send to the transit server to forward and to the remote server to decrypt it. And the protocols should be implemented in the application layer, which means you have to used some applications to use it, such as Shadowsocks, V2Ray, Clash, Surge, etc.
- There still exists some issues, the application can only address the traffic which it can takes over. It(Without TUN mode) can not deal with the traffic which is on the OS layer, such as the UWP, some banks software, etc.
- The tun mode which can virtualize the network interface, and forced take over all the traffic.
- Hardware Proxy: can also called as router proxy, which is the end of whole internet. But the issue is that some router are not designed for this purpose, so the computing ability cannot meet the requirements of encryption and decryption.
- Gateway Proxy: it is usually implemented by the software installed on the PC, and via the CPU, it can easily complete the tasks. And you can change the nodes in the software.
Ratio #
The most suppliers will take all the traffic (upstream and downstream) into account.
The ratio between the traffic you consume and the traffic the supplier statistics.
eg. You use the 0.5x ratio node, and you consume 100G, then the supplier statistics is 50G.
Why there are different ratio nodes?

- The ratio is related to the line quality and user experience.
- Now the supplier have two types of lines:
- Direct line: The line is directly connected to the overseas proxy server via public network. But the transmission effect is poor because the interconnection bandwidth between the overseas operator and the domestic operator is limited, and the domestic operator usually limits the speed of the data flow from the mainland. Besides, if you are the customer of unicom and the overseas server optimize the telecom, then you will get poorer performance than the telecom customer.
- Transit line: Add the transit server, which means the traffic will be transit through the server, hence the traffic is cost in every transit server, so the ratio is high. But it can provide more stable and faster service.
- BGP transit: The domestic transit server will provide the BGP, so you will have a better experience. Normally, it will use some tunnel protocols to balance the traffic and improve the stability.
- IPLC transit: Transit through the IPLC eg. SZ-HK, and then from HK to overseas proxy server.
Latency #
Note: The RTT is not the speed. The RTT is just the building time of the connection. The speed will depend on the shortcomings of the whole network.
PING #
ping aims to send a ICMP request to the target host and wait for the response.
The program will estimate the loss rate of data packets and the round-trip delay time based on the time and the number of successful responses.
icmp ping: the classic ping. It test the latency between the machine and the transit server.tcp ping / http ping: It test the latency of the data packages of corresponding protocol. Normally, it will be slower than the icmp ping.
Node selection mechanism #
- Load balancing
- url-test: It normally send the request to specific url, and select the best node.
- fallback
- SSID
Strategy #
Traffic diversion #
The traffic diversion is the strategy that can distribute the traffic to the different server, which can speed up the access speed.
PAC1 #
Proxy auto config which is a method of web proxy. It can automatically select the suitable proxy server and only affect the browser.
It mainly depends on the specific rules which maintained by community, such as gfwlist.
Router traffic diversion #
For traffic diversion in the routing table, you can refer to SSR-win. There are PAC diversion rules and routing diversion. For routing diversion, you need to add a SOCKS5 proxy in the browser by yourself or use Proxifier to set up a system proxy. Similarly, the settings of V2RayN on Windows also involve routing diversion. As for SS/SSR on Android, it is based on ACL (Access Control List) diversion, and there are ACLs made by third parties. On iOS, there is rule-based diversion. Since common protocols themselves don’t stipulate how to conduct diversion, it is all achieved by the software itself.
Strategy diversion #
proxy, direct, reject
Socks5 #
Socks5 is the protocol of the Session Layer, which is lower than the HTTP protocol. Socks5 mainly focus on the data package transmission, and it is not concerned with the specific protocol and usage.
Socket is more like a “どこでもドア” in Doraemon, it needs the source IP and port and destination IP and port. The developer only needs to send the data to the Socket and get data from the Socket. The details of transport are transparent to the developer.
VPN vs Socks5 #
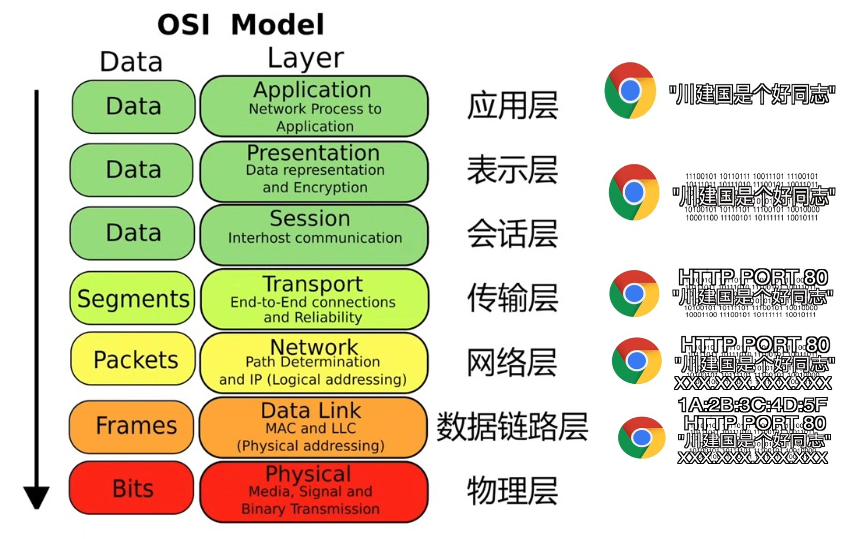
The OSI model is shown as above.
The Application Layer you search a query on the browser, and the browser sends it to the Presentation Layer via http.
The Presentation Layer translate the query to the machine language and sends it to the Session Layer.
The Session Layer maintains the session between the client and the server.
The Transport Layer defines the protocol and the port.
The Network Layer adds the IP address.
The Data Link Layer adds the MAC address.
The Physical Layer sends the data in bits.
VPN is the same as virtual network interface, it will take over all the traffic. You can refer to the image below.
So we can find that the Socks5(without TUN mode) cannot proxy the traffic of online games, and the network commands.
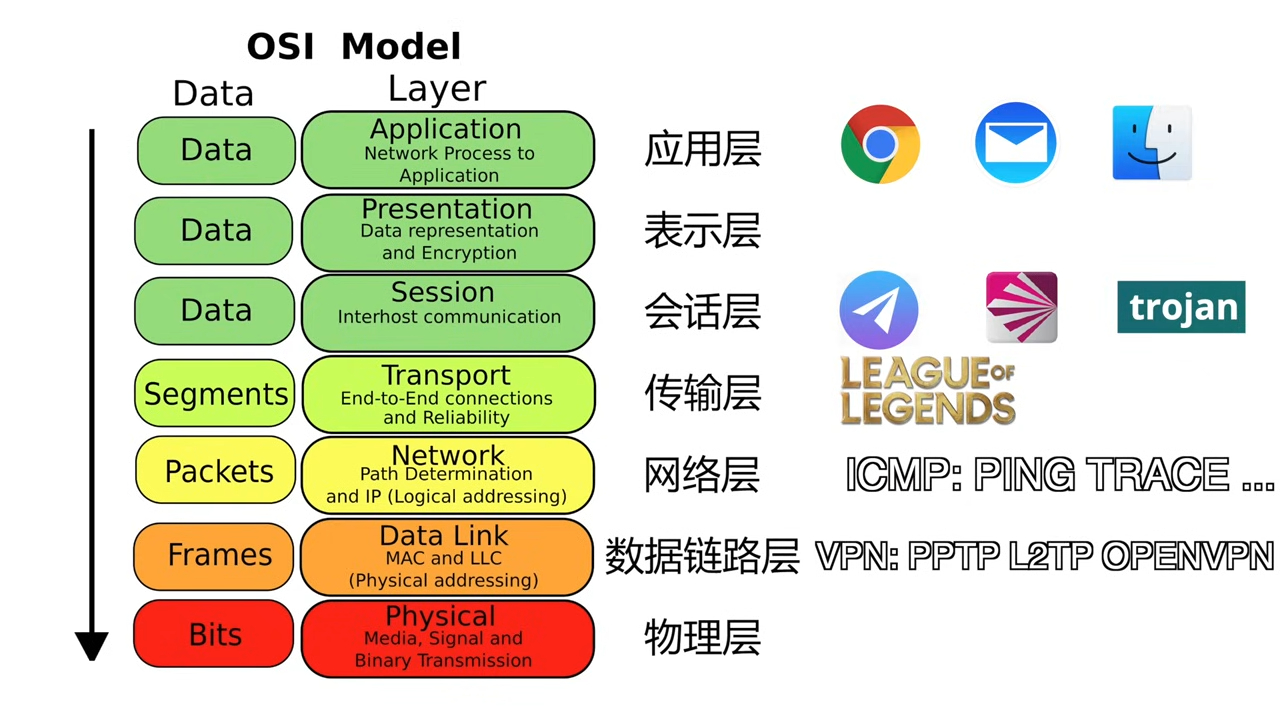
The most VPN is used the TCP protocol, it needs to establish a connection, so it can be interupted by the reset packet. Besides, the feature of the VPN is very clear, so it is easy to be detected.
Nowadays, A new VPN called wireguard used the UDP protocol, so it cannot be interupted by normal methods. But it will be limited the speed in QoS.
Reference:
- https://www.rfc-editor.org/
- https://www.youtube.com/watch?v=wAxOjL_gDzk
- https://www.duyaoss.com/archives/1086/
- https://mp.weixin.qq.com/s/2teDwwIhyZ6BYIEQ_HL1vQ
- https://zhuanlan.zhihu.com/p/64467370
- https://doubibackup.com/6r9z6_wi-2.html
- https://www.duyaoss.com/archives/2741/
- https://blog.revincx.icu/posts/proxy-summary/index.html
- https://ephen.me/2017/PublicDns_1/
- https://www.youtube.com/watch?v=Ty0n7AgcX0w
If you find this blog useful and want to support my blog, need my skill for something, or have a coffee chat with me, feel free to: