The Overview of Security
January 8, 2025 · 6 min read · Page View:

The Overview of Security
If you have any questions, feel free to comment below. Click the block can copy the code.
And if you think it's helpful to you, just click on the ads which can support this site. Thanks!
In today’s digital age, security is paramount. As we increasingly rely on technology for communication, commerce, and data storage, understanding the fundamentals of security becomes essential. This article provides an overview of key security concepts, including encryption, digest algorithms, and digital signatures. By exploring these topics, we aim to equip you with the knowledge to protect your digital assets and ensure the integrity and confidentiality of your information. Whether you’re a tech enthusiast or a professional in the field, this guide will offer valuable insights into the mechanisms that safeguard our digital world.
Encryption #
Symmetric Encryption #
The same key is used for both encryption and decryption. The key is normally short. And the efficiency is high, so it is widely used in https communication and network transmission.
The most common symmetric encryption algorithm is AES, DES, 3DES, DESX, Blowfish, RC6.
Asymmetric Encryption #
The public key and the private key are used for encryption and decryption. The public key is widely distributed, while the private key is kept secret. Only the holder of the private key can decrypt/encrypt the data encrypted/decrypted by the public key.
Cons: The efficiency is low, it will take a long time to encrypt/decrypt the data. So it is only suitable for small data encryption. e.g. https communication pre-shared key、CA certificate、login authentication.
The most common asymmetric encryption algorithm is RSA, ECC, DSA, ECDSA, Diffie-Hellman.
- The symmetric encryption can not be used for signing, only the asymmetric encryption can be used for signing.
- Verify file consistency will use the Information Digest Algorithm.
Digest Algorithm #
The digest algorithm is usually called as the hash algorithm.
- It is a one-way encryption algorithm, which means that the original data can not be restored from the encrypted data.
- It will generate a fixed length of data, which is called the digest.
- The digest is unique for the original data, and the same original data will generate the same digest(in the same hash algorithm).
- Avoid collision.
- Normally can be considered as the compression of the original data.
Above all, so it can be used for file integrity verification.
MD series #
MD2、MD4、MD5, and the MD5 is the most common one as well as secure and fast.
MD5(Message Digest Algorithm): Generally generate a 128-bit hash value(16 bytes), and the output is a 32-character hexadecimal string. Normally generate the .md5 or .md5sum file to make sure the file is not modified.
SHA series #
SHA (Secure Hash Algorithm): The length of SHA is longer than MD, so it is more secure to avoid collision. But the speed is lower than MD.
SHA1 generate a 20 bytes(160 bits) hash value, SHA224 generate a 28 bytes (224 bits) hash value, SHA256 generate a 32 bytes(256 bits) hash value, SHA384 generate a 48 bytes(384 bits) hash value, SHA512 generate a 64 bytes(512 bits) hash value.
Digital Signature #
Normally, the digital signature will use the hash algorithm to generate the digest, and then use the asymmetric encryption algorithm to sign the digest.
The process is as follows:
Sender:
- Use the hash algorithm to generate the digest of the original data.
- Use the sender’s private key to encrypt the digest.
- Send the original data and the encrypted digest to the receiver.
Receiver:
- Use the hash algorithm to generate the digest of the received data.
- Use the sender’s public key to decrypt the digest.
- Compare the decrypted digest with the received digest. If they are the same, it means that the data is not modified.
encrypt(hash(plaintext), private_key_a) =============== (plaintext, signature) ===============> hash(plaintext) == decrypt(signature, public_key_a) ?
However, this only resolve the Imitation and Tampering problem. But can not resolve the tapping problem. Because the text in the network is plaintext, and anyone who has the public key can decrypt the text. How about another way?
encrypt(plaintext, public_key_b) =============== ciphertext ===============> decrypt(ciphertext, private_key_b)
This way can resolve the tapping and Tampering problem(Because the three party can not get the receiver’s private key). But it can not resolve the Imitation problem.
So we can combine the two ways to make the data more secure. That is first use the public key to encrypt the plaintext, and then use the private key to sign the hash of the plaintext.
encrypt(plaintext, public_key_b), encrypt(hash(plaintext), private_key_a) =============== (ciphertext, signature) ===============> plaintext = decrypt(ciphertext, private_key_b), hash(plaintext) == decrypt(signature, public_key_a) ?
However, this process still has some problems:
- The performance is low, because the asymmetric encryption is slow.
- If the distribution of public key is not secure, the attacker can temper the public key to his own public key, the tunnel will be intercepted by the attacker.
For the performance issue #
We can also use the symmetric encryption to encrypt the plaintext, but how to distribute the symmetric key is another problem. In deed, we often use the asymmetric encryption to encrypt the symmetric key. And then use the symmetric encryption to encrypt the plaintext and transfer.
For the public key distribution issue #
To make sure the public key is correct, the public key will be signed by the CA. And CA will sign the public key with its private key and send them both (Digital Certificate) to the receiver. Then the receiver can use the CA’s public key to decrypt Digital Certificate to get the sender’s public key.
In the ssl/tls protocol, the most common situation is the http. The process is as follows:
- The server developer register a domain and apply for a certificate from the CA.
- The server prepare an asymmetric key pair. Provide the information about the domain, and the public key
public_key_serverto the CA. - The CA will verify the information, and then sign the public key with its private key to generate the Digital Certificate.
server_certificate = (domain, validity, issuer, public_key_server, ..., signature = (encrypt(hash(domain, validity, issuer, public_key_server, ...), private_key_ca))) - The server can deploy the
server_certificateand the private key, then provides the service.
- The server prepare an asymmetric key pair. Provide the information about the domain, and the public key
- The client normal already has the
CA's public key, so when the client request the server, the client will receive theserver_certificate. Then use the CA’s public key to verify the certificate and get thepublic_key_server.server ===== server_certificate =======> client: hash(domain, validity, issuer, public_key_server, ...) == decrypt(signature, public_key_ca) ? - Then the client will generate a symmetric key, and use the
public_key_serverto encrypt the symmetric key. Then communicate with the server using the symmetric key.
Moreover, the actual process is more complex, eg, the https uses the Two-way certification.
In https step3, the client will send the client_certificate which contains the public_key_client to the server. The server will verify the certificate and get the public_key_client via the root certificate.
Then send the supported cipher suite list to the server, the server will choose one cipher suite and send the suite via public_key_client to the client. Then generate the symmetric key and communicate with the server using the symmetric key.[1]
Maybe you have attention the root certificate in the above process. What’s this?
In deed, there is a certificate chain[2], as you can find in the browser:
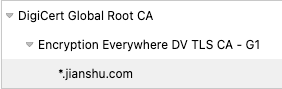 Certificate Hierarchy
Certificate HierarchyThe end-entity certificate is the certificate of the server *.jianshu.com, and the intermediate certificate is the certificate of the CA. The root certificate is the certificate of the CA’s CA.
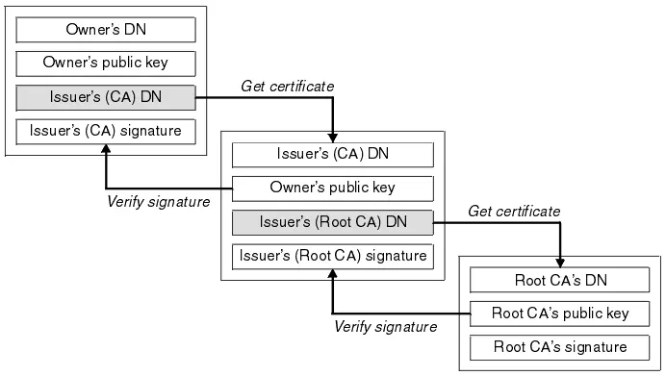 Certificate Chain
Certificate ChainSo where is the root certificate? Normally, the root certificate is installed in the browser or device OS(trusted root certificates), eg Lists of available trusted root certificates in macOS[3]. Also you can download to install it.
Digital signature algorithm #
RSA signature algorithm is the most common one. Such as MD5withRSA means use the MD5 hash algorithm to generate the digest, and then use the RSA algorithm to sign the digest.
DSA (Digital Signature Algorithm): It is a digital signature algorithm based on the discrete logarithm problem. Only can be used for signing, not for encryption.
ECDSA (Elliptic Curve Digital Signature Algorithm): It is a digital signature algorithm based on the elliptic curve. Secure and fast.
References
If you want to follow my updates, or have a coffee chat with me, feel free to connect with me: